
4.5 (433) · $ 145.00 · In stock
Description
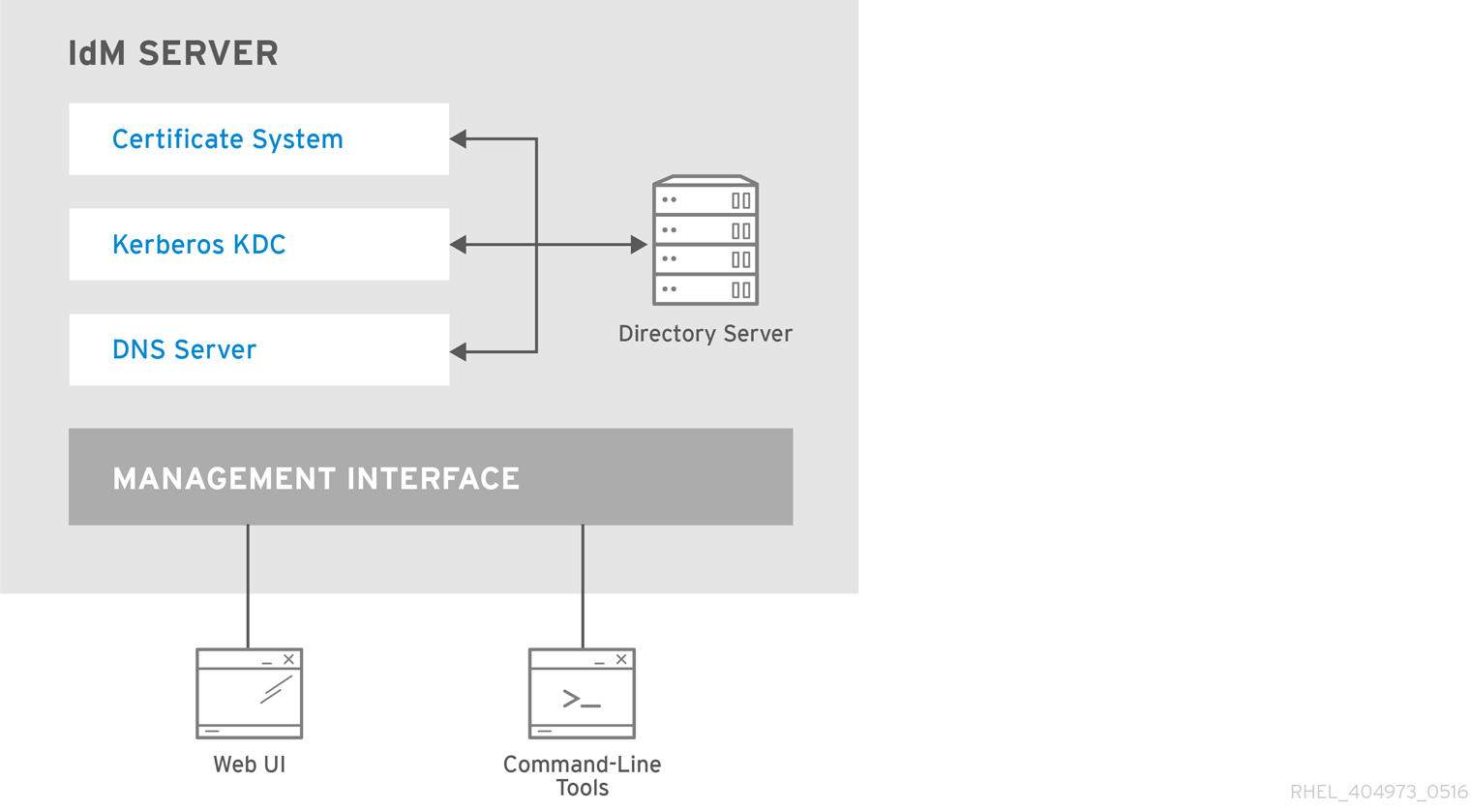
Configuring and managing Identity Management Red Hat Enterprise Linux 8

SLC User Guide Datasheet by Lantronix, Inc.

Authenticate This LV: READ the rules & use the format in post #1, Page 427
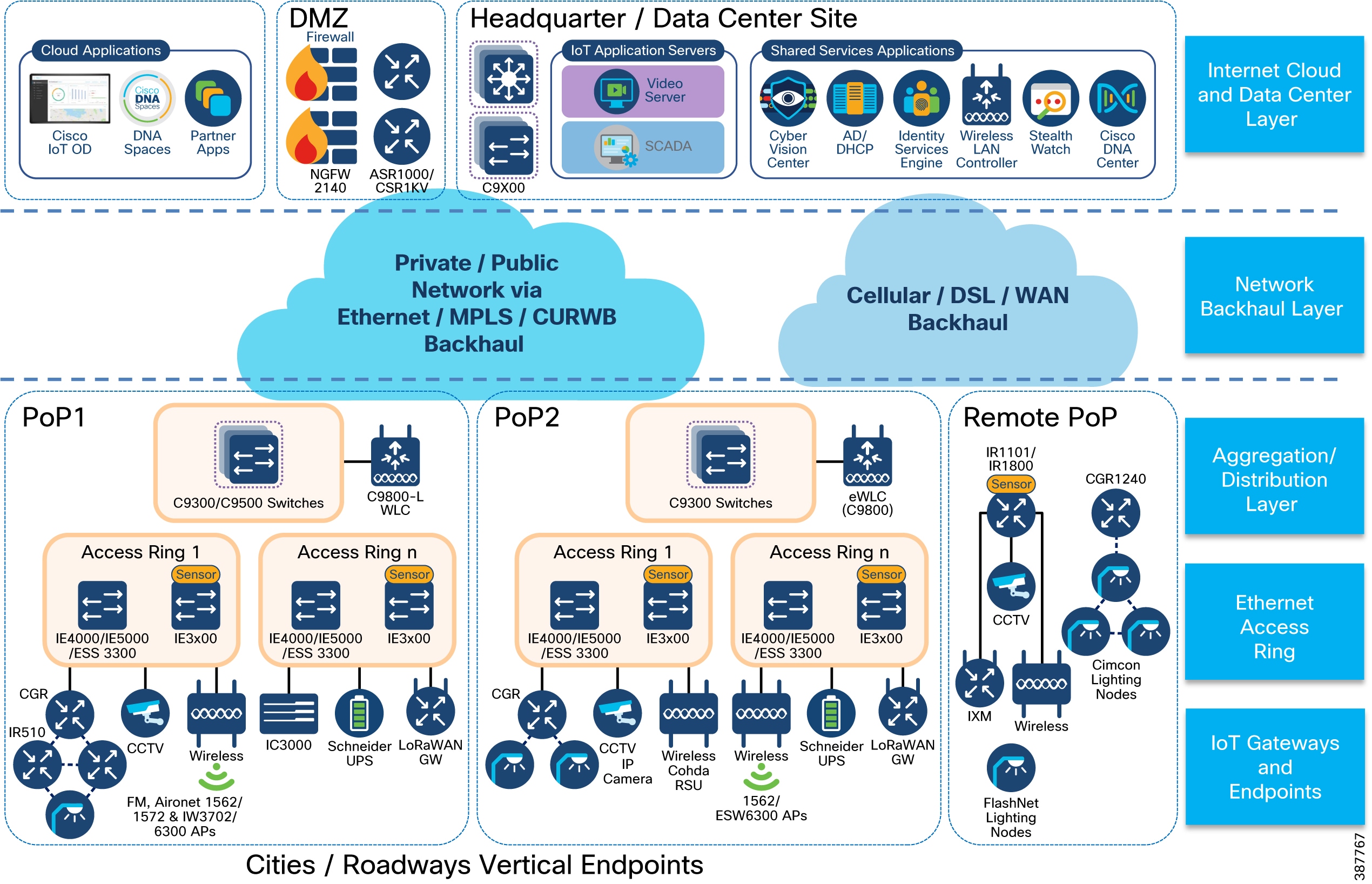
Connected Communities Infrastructure Solution Implementation Guide - Connected Communities Infrastructure Solution Implementation Guide [Solutions] - Cisco
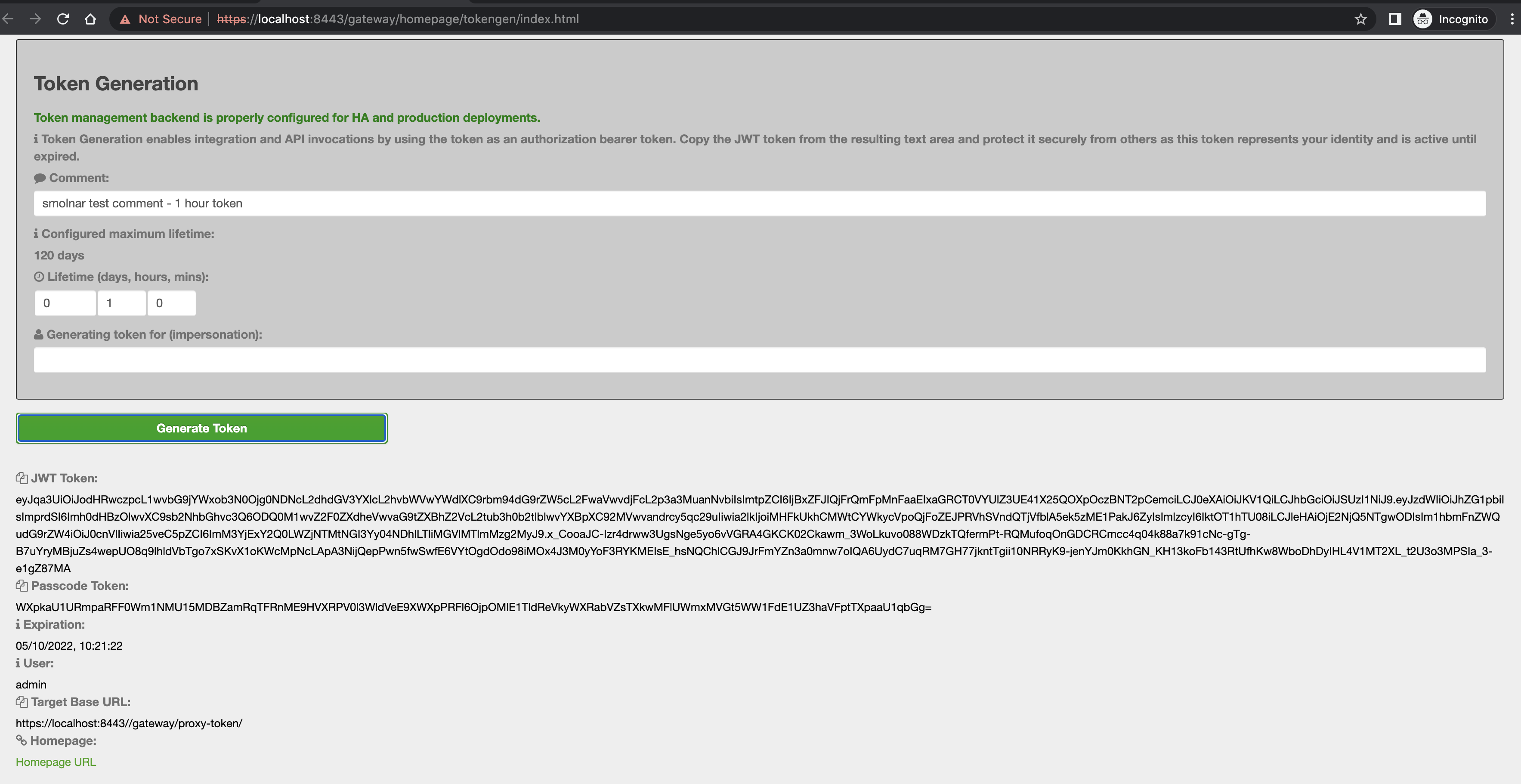
Knox Apache User-guide
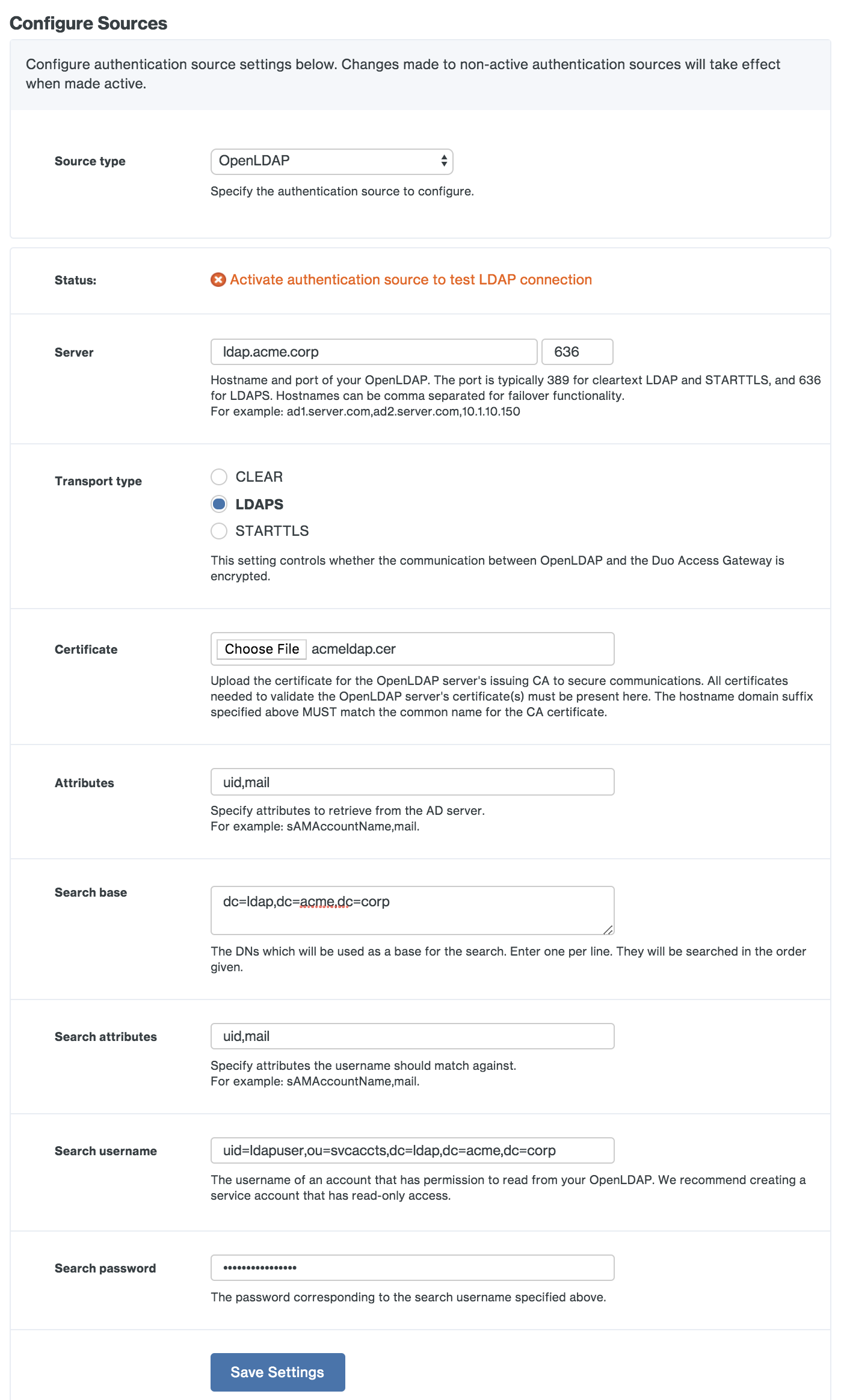
Duo Access Gateway for Linux

Pwning Printers with LDAP Pass-Back Attack, by Nairuz Abulhul, R3d Buck3T

12 13 admin handbook 7 10 13 by Charisse Giseburt - Issuu
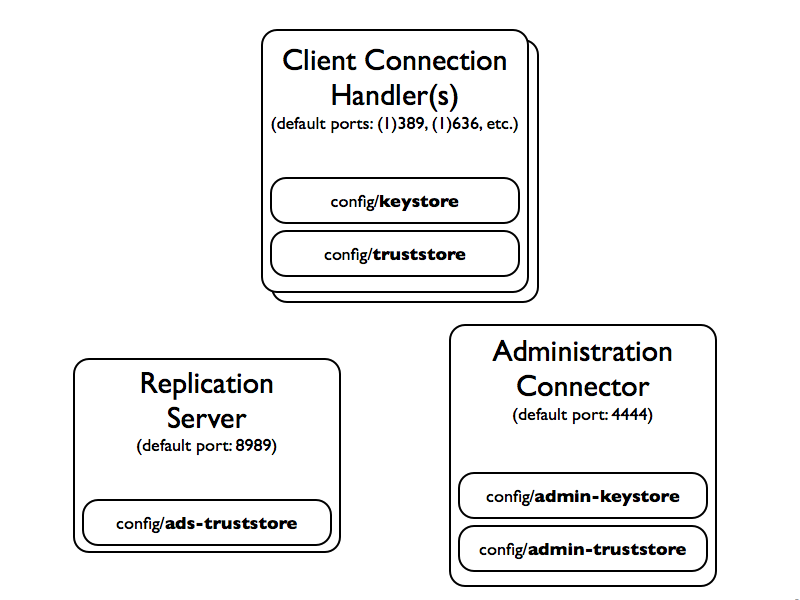
OpenDJ 3 > Administration Guide

Analytical Methodologies for Agrometallomics: A Critical Review

Authenticate This LV: READ the rules & use the format in post #1, Page 389